NanoSSH
3 minute read
DigiCert® TrustCore SDK NanoSSH is a lightweight, standards-compliant SSH-2 client and server built for straightforward integration with embedded devices, cloud-native workloads, network hardware, and other diverse platforms. It offers built-in RADIUS and X.509v3 certificate authentication and runs on virtually any OS or CPU with minimal memory overhead.
NanoSSH is available in two models:
License
This project is available under a dual-license model:
- Open Source License: GNU Affero General Public License v3 (AGPL v3): This license allows you to use, modify, and distribute the code for free in accordance with AGPL terms.
- Commercial License: If you wish to use TrustCore SDK in a proprietary or commercial product (e.g., embedded in closed-source firmware or commercial SaaS applications), a commercial license is available under DigiCert’s Master Services Agreement (MSA). Contact us at sales@digicert.com for commercial licensing details.
Cryptography options
NanoSSH can use the NSA Suite B cipher set (ECC, AES-GCM, SHA-2) when you link against NanoCrypto Advanced or the NanoCrypto FIPS module. TrustCore SDK includes NanoCrypto basic by default, which omits Suite B and FIPS mode.
What you can do
- SSH client shell: open an encrypted terminal session to execute commands on a remote host.
- SSH client port forwarding: wrap any TCP stream in an SSH tunnel for secure point-to-point transport.
- SSH/SFTP server: accept connections from NanoSSH or any SSH 2 client to provide remote shell, file transfer, or tunnelling services.
With a single ANSI-C codebase, NanoSSH brings strong, certificate-backed security to resource-constrained products without the licensing or size penalties of larger SSH stacks.
Key features
NanoSSH provides the following features:
- Small memory footprint
- Speeds integration and testing of complex cryptographic functions for your product
- SSHv2 compliant
- TCP/IP-neutral
- Certificate support, per IETF draft 3, http://tools.ietf.org/html/draft-ietf-secsh-x509-03
- Re-keying at will, based on a specified number of packets or a certain amount of time
- OS- and platform-agnostic for easy portability
- Threadless architecture, synchronous and asynchronous
- Guaranteed GPL-free code that protects your intellectual property
System requirements
Supported operating systems
- Linux: Ubuntu, Debian, Raspbian, CentOS, Yocto, OpenWRT
- BSD / Unix: FreeBSD, Solaris
- Windows: Microsoft Windows, Cygwin
- RTOS: Zephyr RTOS
Tip
Need something else? NanoSSH can be ported to additional POSIX-compatible OSes or embedded RTOSs. Contact your DigiCert® account representative to learn more.Supported processor and accelerator platforms
- CPUs: Intel® x86, ARM® Cortex-A / Cortex-M, MIPS® 32
- Hardware acceleration: Intel® AES-NI; vendor extensions via NanoCrypto callbacks
- Secure elements: TPM 1.2
Supported standards
NanoSSH supports the following RFC standards:
- SSH File Transfer Protocol, v2, v3 and v4
- RFC 4250: The Secure Shell (SSH) Protocol Assigned Numbers
- RFC 4251: The Secure Shell (SSH) Protocol Architecture
- RFC 4252: The Secure Shell (SSH) Authentication Protocol
- RFC 4253: The Secure Shell (SSH) Transport Layer Protocol
- RFC 4254: The Secure Shell (SSH) Connection Protocol (partially supported)
- RFC 4344: The Secure Shell (SSH) Transport Layer Encryption Modes
- RFC 4335: The Secure Shell (SSH) Session Channel Break Extension
- RFC 4419: Diffie-Hellman Group Exchange for the Secure Shell (SSH) Transport Layer Protocol
- RFC 4432: RSA Key Exchange for the Secure Shell (SSH) Transport Layer Protocol. For detailed information refer to section 7 of the RFC draft-ietf-secsh-filexfer-03.txt, SSH File Transfer Protocol (http://tools.ietf.org/html/draft-ietf-secsh-filexfer-03).
- RFC 6187: X.509v3 Certificates for Secure Shell Authentication
- RFC 6239: Suite B cryptographic suites for SSH
- Draft-green-secsh-ecc-07: Elliptic-Curve Algorithm Integration in the Secure Shell Transport Layer
- Draft-igoe-secsh-aes-gcm-02: AES Galois Counter Mode for the Secure Shell Transport Layer Protocol
- Draft-josefsson-ssh-chacha20-poly1305-openssh-00 - ChaCha20 Poly1305 for the Secure Shell Transport Layer Protocol
- Draft-ietf-curdle-ssh-ed25519-02 - Ed25519 for Secure Shell Transport Layer Protocol
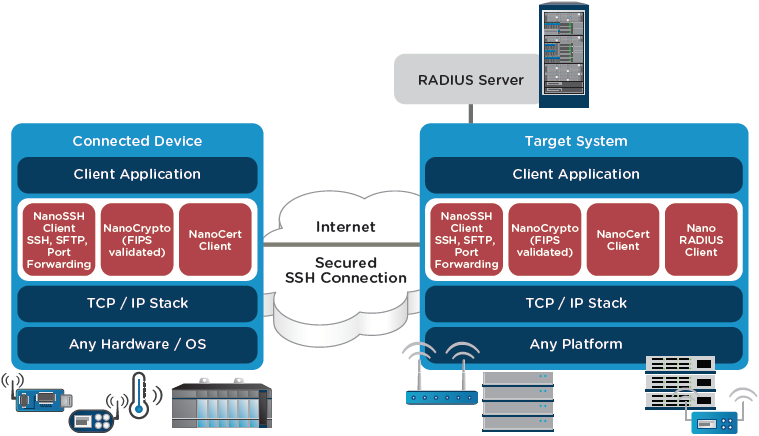
Network architecture diagram
The figure below shows how NanoSSH is implemented to protect target systems and their connected devices.