NanoSSL
6 minute read
DigiCert® NanoSSL is a TLS/SSL solution specifically designed to speed product development while providing device security services for resource-constrained environments. With the Internet of Things (IoT), several types of network-connected devices need secured management access to transport data securely over the unsecured Internet.
TLS/SSL (Transport Layer Security/Secure Sockets Layer) authenticates endpoints and encrypts channels to provide session privacy and security on the Internet. SSL operates at the transport layer in the OSI stack and provides secured data transport to applications. It supports peer negotiation for algorithm selection, public key-based exchange of secret session keys, and X.509 certificates.
NanoSSL provides easy-to-use APIs for integration with applications like web servers and browsers. Its certificate management module allows it to fetch or renew SSL certificates, check the status of SSL certificates using CRLs, or to query a Certificate Authority (CA) or certificate chain.
NanoSSL also supports NSA Suite B crypto algorithms to provide a holistic approach for securing networked devices and services, ideally suited for high-traffic enterprise and federal environments where performance is critical. Suite B cryptography is a set of cryptographic algorithms and protocols specified by NIST that are approved by the NSA for protecting classified and unclassified National Security Systems (NSS).
NanoSSL is available in two models:
License
This project is available under a dual-license model:
- Open Source License: GNU Affero General Public License v3 (AGPL v3): This license allows you to use, modify, and distribute the code for free in accordance with AGPL terms.
- Commercial License: If you wish to use TrustCore SDK in a proprietary or commercial product (e.g., embedded in closed-source firmware or commercial SaaS applications), a commercial license is available under DigiCert’s Master Services Agreement (MSA). Contact us at sales@digicert.com for commercial licensing details.
Key features
DigiCert NanoSSL provides the following features:
- Small memory footprint
- Accelerates integration and testing of complex cryptographic functions for your product
- FIPS 140-2/3 Level 1 validated (optional)
- Integration with the Enrollment over Secure Transport (RFC-7030)
- TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3 compliant
- OpenSSL Connector for migration from open source with API level equivalency (with turnkey professional services)
- Operators for hardware acceleration
- Crypto abstraction platform for compliance with export/import controls
- SSLv3 (RFC 7568) compliant
- SSLv3 is disabled by default in NanoSSL but can be enabled if necessary to support communication with legacy applications that require SSLv3
- TCP/IP-neutral
- Pre-shared keys
- SSL alerts
- Support for TLS server name extension (RFC 6066)
- Support for mutual authentication
- Support for DTLS 1.2 and 1.3
- Support for PKCS#8 and PKCS#12 certificate formats
- Support for TPM-generated keys
- OS- and platform-agnostic for easy portability
- Threadless architecture, synchronous and asynchronous
- Guaranteed GPL-free code protects your intellectual property
System requirements
Memory requirements
NanoSSL has a minimum memory footprint of 156KB.Estimate based on Intel x86 builds.
Typical memory usage is with a full set of ciphers and may vary (decrease or increase) based on 32/64-bit, x86/ARM/MIPS, reduced set of ciphers, static/shared library, and compile flags.
Supported operating systems
NanoSSL is currently supported on the following operating systems:
- Linux (Ubuntu, Debian, Raspbian, CentOS)
- Solaris
- Microsoft® Windows
- Cygwin
- FreeBSD
- QNX
- FreeRTOS
- VxWorks
- ThreadX
Note
DigiCert can provide a guide to assist with porting to another operating system or RTOS. To learn more, contact your DigiCert account representative.Supported operating platforms
NanoSSL is currently supported on the following operating platforms:
- Intel® x86
- ARM Cortex
- Hardware Acceleration - Intel AES-NI, Vendor Extensions via NanoCrypto Callbacks
- Secure Element - TPM 1.2, TPM 2.0, ARM TrustZone, PKCS11
- VxWorks 6.9 and 7.0 Workbench IDE
- OPC-UA HP SDK for Linux and Windows platforms
OpenSSL compatibility
TrustCore SDK makes it easy to replace the OpenSSL SSL and crypto library with a shim that uses the NanoSSL and NanoCrypto implementation, so you don’t have to change your application calls. To learn more about replacing OpenSSL with NanoSSL, refer to About DigiCert OpenSSL Connector provided by DigiCert.
Supported standards
DigiCert NanoSSL supports the following standards:
- RFC 2246: TLS Protocol Version 1.0
- RFC 3268: Advanced Encryption Standard (AES) Cipher suites for TLS
- RFC 6066: Transport Layer Security (TLS) Extensions
- RFC 4279: Pre-shared Key Cipher suites for TLS
- RFC 4346: TLS Protocol Version 1.1
- RFC 4492: Elliptic Curve Cryptography (ECC) Cipher Suites for Transport Layer Security
- RFC 5077: Transport Layer Security (TLS) Session Resumption without Server-Side State
- RFC 5246: The Transport Layer Security (TLS) Protocol Version 1.2
- RFC 5280: Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile (obsoletes RFC 3280)
- RFC 5288: AES Galois Counter Mode (GCM) Cipher Suites for TLS
- RFC 5289: TLS Elliptic Curve Cipher Suites with SHA-256/384 and AES Galois Counter Mode (GCM)
- RFC 5430: Suite B Profile for Transport Layer Security (TLS)
- RFC 5487: Pre-Shared Key Cipher Suites for TLS with SHA-256/384 and AES Galois Counter Mode
- RFC 5489: ECDHE_PSK Cipher Suites for Transport Layer Security (TLS)
- RFC 5746: TLS Renegotiation Indication Extension
- RFC 6066: Transport Layer Security (TLS) Extensions: Extension Definitions
- RFC 6101: Secure Sockets Layer (SSL) Protocol Version 3.0
- RFC 6520: Heartbeat Extension for TLS and DTLS.
- RFC 6655: AES-CCM Cipher Suites for Transport Layer Security (TLS)
- RFC 7251: AES-CCM Elliptic Curve Cryptography (ECC) Cipher Suites for TLS
- RFC 7568: Deprecating Secure Sockets Layer Version 3.0
- RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3
- RFC 9146: The Datagram Transport Layer Security (DTLS) Protocol Version 1.3
FIPS and Suite B support
The Federal Information Processing Standard (FIPS) Publication 140‑2 and 140-3 are U.S. government computer security standards used to accredit cryptographic modules. FIPS 140‑2/3 validation is a requirement when selling products containing embedded cryptography to the U.S. government, and the standards have been increasingly adopted as baseline requirements by regulated industries such as finance, manufacturing and healthcare.
The National Institute of Standards and Technology (NIST) established the Cryptographic Module Validation Program (CMVP) that validates cryptographic modules to FIPS 140‑2/3 (see http://csrc.nist.gov/groups/STM/cmvp). For information about the FIPS 140‑2/3-certified NanoCrypto FIPS binary, refer to the NIST web site at http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401vend.htm.
Note
To obtain FIPS 140‑2 or 140-3 certification for your product, a licensed NanoCrypto FIPS binary must be purchased, integrated and tested with your product using our FIPS Validation as a Service offering. For more information, contact Sales.Suite B cryptography is a set of cryptographic algorithms and protocols specified by NIST that are approved by the NSA for protecting classified and unclassified National Security Systems (NSS). If your TrustCore SDK product is used with the TrustCore SDK FIPS binaries, then the Suite B algorithms are already included.
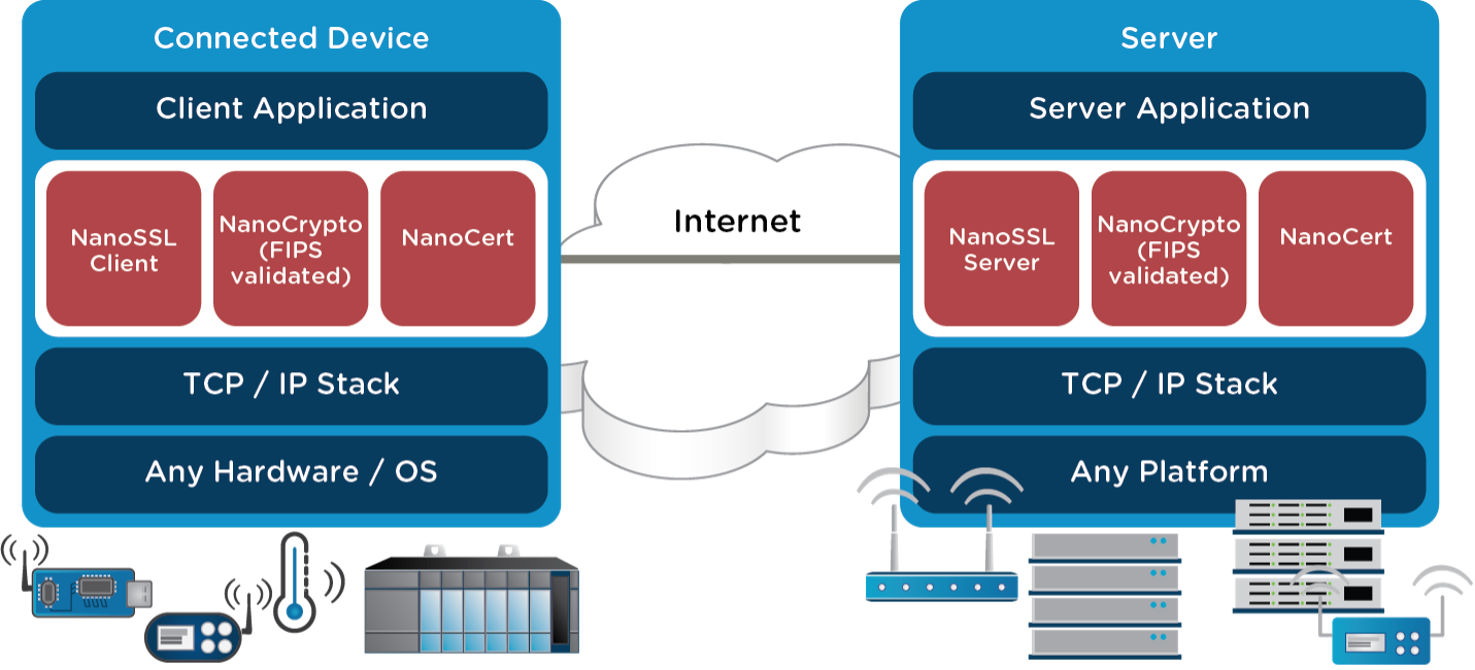
Network diagram
This figure shows how NanoSSL is implemented in a network to securely transfer information between a server and connected devices.
NanoSSL Network Diagram